11 WordPress Security Issues And Vulnerabilities You Should Know About
WordPress is the world’s leading content management system, used by two out of every five websites online. Its flexibility and user-friendliness have contributed to its rise, but this popularity also makes WordPress a frequent target for cyberattacks.
Despite advancements in security features, WordPress sites remain susceptible to various threats, including malware, phishing, and bots. A single security breach can severely damage your brand, disrupt traffic, and impact revenue. That’s why understanding WordPress-specific vulnerabilities is crucial. This article outlines eleven common security issues you may encounter and offers actionable steps to safeguard your WordPress site.
11 WordPress Security Issues and Vulnerabilities You Should Know About
Here are the eleven most common WordPress security issues and vulnerabilities you should know about, followed by steps you can take to mitigate them:
-
Outdated WordPress Core
The WordPress Core has a new update every three months or so. In order to shield the sites from cyberattacks, users are encouraged to download these updates as soon as they are available, manually or automatically. The updates often encompass a variety of improvements, bug fixes, and essential security patches to address any potential vulnerabilities.
Failure to do so can harm your site’s operation, performance, and compatibility. An outdated Core also prevents you from downloading plugins and themes, leaving room for security breaches.
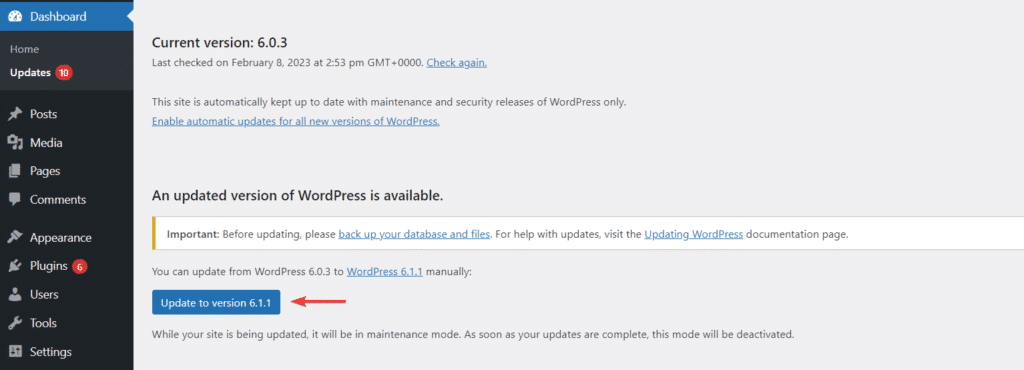
How to Solve This?
WordPress Core versions update automatically. You can check for the latest update on your dashboard. Go to your WordPress Dashboard and navigate to Updates. Even though your WordPress site appears to be functioning flawlessly, your inability to implement changes today could have disastrous effects on your site. -
Outdated Themes and Plugins
One of the biggest reasons behind the popularity of WordPress is its huge library of themes and plugins. These allow users to customize their websites based on their unique business needs. However, these extensions require site owners to be extra cautious and update them frequently to enable additional security.
In this case, updates may contain security patches that prevent malicious entities from using outdated extensions as entry points. They sometimes cause the website to break down, but it is essential to install them nonetheless.
How to Solve This?
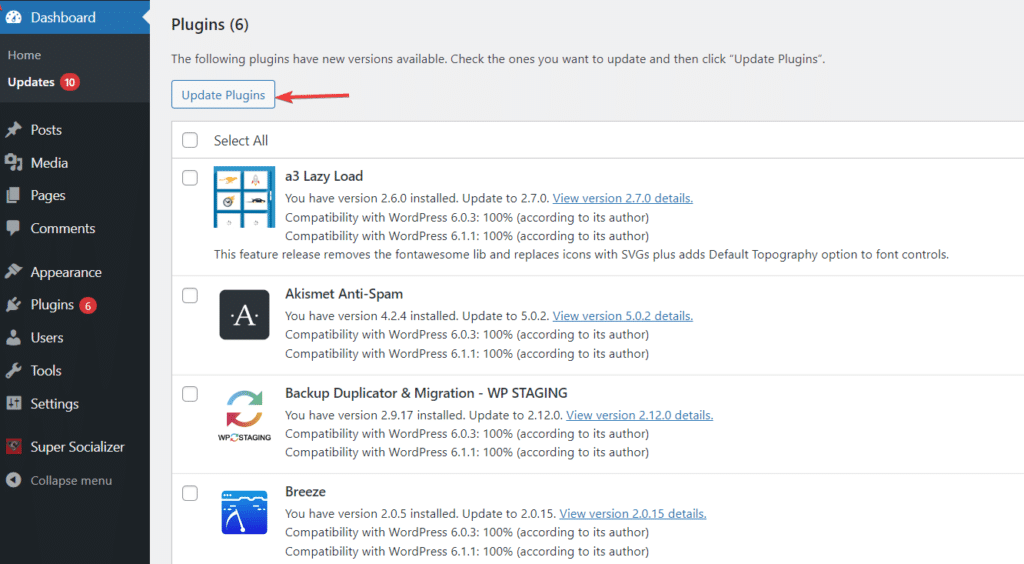
Install updates whenever they are available for themes and plugins. You can manually update them or set up a plugin that automatically updates them. To update plugins from your dashboard, go to the WordPress Dashboard, navigate to Plugins, and click on Update Plugins. This will update all the plugins you use along with your website.
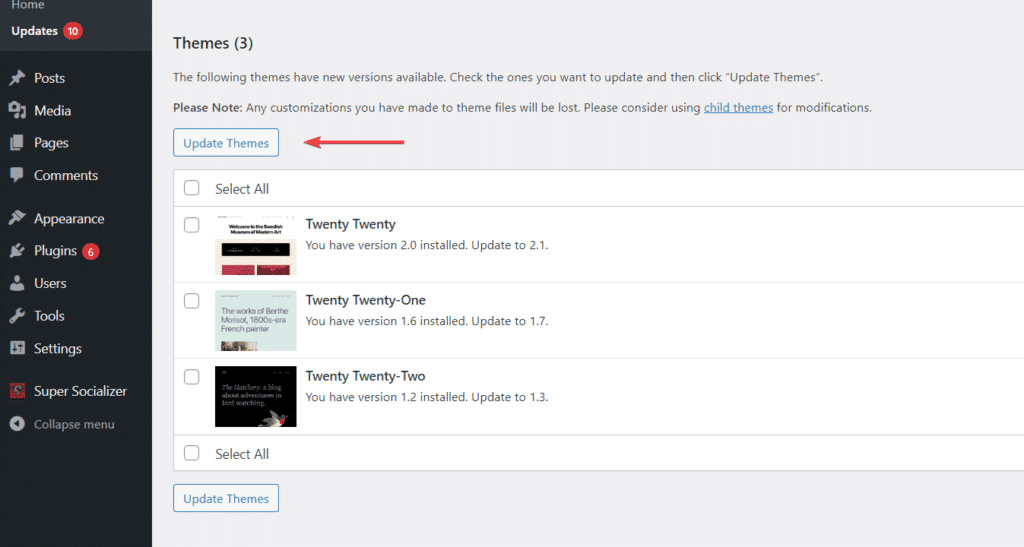
To update themes from your dashboard, open your WordPress Dashboard, navigate to Themes, and click on Update Themes.
-
Unauthorized Logins
Outdated plugins and weak passwords often make WordPress sites vulnerable to unauthorized logins, commonly through brute force attacks. These attacks involve repeated password-guessing attempts, often automated by bots.
The reasons why brute force attacks are so common are:
- The default WordPress login page is easy to find, and
- Many site owners use weak credentials.
Unauthorized access can severely compromise your digital infrastructure, posing significant risks to your website.
How to Solve This?
You can employ the following actions to prevent this problem:- Change the default wp-admin login URL to make it more difficult for hackers to attack your WordPress website using brute force;
- Integrate WordPress with Google’s invisible reCAPTCHA; and,
- Use robust and unique passwords for all websites, including social media and email accounts.
- Employ multi-factor authentication, asking users to verify login from a second device, wherever applicable.
It is also crucial to uphold the principle of least privilege, according to which only the barest number of contributors should have access to restricted capabilities. Remember that brute force attacks are applicable anywhere there is a requirement for a password, so fortify login pages for any password-protected information.
-
Malware Infections
Malware is an umbrella term for any code that allows unauthorized access to your site. Malware can be challenging to avoid due to its wide variety of forms, including malicious redirects, drive-by downloads, and spyware.
Hackers can insert malicious code into already-existing files to steal data or create “backdoors” for further unauthorized actions.
In many cases, you may have to entirely delete the corrupted file or retrieve a previous site version from the backup. This is why it is imperative to always backup your website information regularly.

How to Solve This?
You can prevent malware from infecting your site by taking the following measures:- Check plugins and themes carefully before installing them,
- Conduct regular security scans to detect any hidden malware inside your systems.
-
Credit Card Skimming
Credit card skimming is a type of malware made to steal the credit card details of your customers. Credit card skimming is a malware threat targeting e-commerce sites on WordPress, designed to steal customer credit card information. Typically, using JavaScript injection, skimmers capture card details during the checkout process.
This malware often gains entry through weak passwords or compromised software, embedding itself in plugins or themes to avoid detection. Once inside the admin area, it gathers as many credit card credentials from your site as possible.
How to Solve This?
You can take the following steps to prevent credit card skimming:- Deploy a monitoring tool to track suspicious activities on your site regularly;
- Keep your site and its components regularly updated with the latest security patches; and,
- Protect the sensitive information on your website by installing firewalls and intrusion detection systems, and get an SSL certificate for your site.
-
Structured Query Language (SQL) Injections
SQL is the primary language for database management in WordPress but is susceptible to SQL injection attacks. These attacks allow hackers to view and modify your site’s database, creating unauthorized accounts or leaking data.
Secure software development practices can help prevent such vulnerabilities from being present in your website’s code. Vulnerabilities often lie in comment boxes and text fields where SQL commands can be inserted. Additionally, adding PHP commands to URLs poses another security risk, enabling attacks on the database and other website components.
How to Solve This?
You can use the steps listed below to stop URL hacking and SQL injection attacks:- Use parameterized queries or prepared statements;
- Check user input;
- Encrypt your data;
- Access with the least privilege;
- Regularly update your database and applications; and,
- Consider using a Web Application Firewall (WAF).
WordPress circumvents this security issue in its own way. Most WordPress websites are hosted on an Apache server using an ingenious technique to thwart these attacks. The .htaccess file on each Apache server specifies the website’s access policies.
-
Supply Chain Attacks
Supply chain attacks target WordPress’s popular features: themes and plugins. These attacks occur either when a plugin owner distributes malware or when a hacker acquires a well-known plugin to insert malicious code through updates.
Either way, attackers gain backend access to your site, compromising secure data and potentially launching additional attacks like SEO spam and phishing. Regularly updating themes and plugins is crucial to mitigating the risk of supply chain attacks.
How to Solve This?
Supply chain attacks tend to get over quickly since WordPress developers are usually very active in identifying phony themes and plugins. However, if one manages to slip between the cracks, adding security plugins that periodically scan your website will rapidly reveal any flaws. You must also back up the data on your WordPress site so you can restore it if it is compromised. -
Search Engine Optimization (SEO) Spam
SEO Spams targets your top-ranking pages and infects them with spammy keywords and phoney adverts, similar to SQL injections. These components may lead users to dubious or harmful websites.
SEO spam may occur because of:
- Outdated themes and plugins,
- Undefined user roles,
- Spammy content,
- Weak security scans.
Two examples of SEO spam malware are the Japanese keyword hack and the pharma hack. They usually manifest as Japanese or pharmaceutical keywords in your search results.


Owing to SEO spam malware, your website may be flagged on the Google Search Console, land on Google’s blacklist, and ultimately, get your hosting account suspended.How to Solve This:
To counter SEO spam:- Keep plugins, themes, and security measures up-to-date.
- Employ strong passwords and two-factor authentication for added security.
- Monitor analytics for sudden SERP changes or traffic spikes to spot issues.
- If code-savvy, manually check high-ranking pages for discrepancies.
No matter which approach you take, it is critical to target and solve these hacks as soon as possible. Failing to address these hacks can lead to penalties from SEO crawlers, nullifying all your hard work.
-
Distributed Denial of Service (DDoS) Attacks
A Denial-of-Service (DoS) attack seeks to prevent website administrators and users from accessing a website. This is accomplished by flooding a targeted server with traffic to the point when it fails, shutting down all hosted websites.
The server and the websites it hosts eventually come back online; however, it could be challenging to repair the reputation of the websites that were assaulted.
When executed from multiple computers, creating a botnet, it becomes a Distributed-Denial-of-Service (DDoS) attack. These attacks can result in significant downtime, performance issues, revenue loss, and reputational damage for WordPress websites.
How to Solve This?
The best defense against a WordPress DDoS attack is secure WordPress hosting. You can combine it with top-tier security plugins for a more layered approach. Here are a few steps you can take to prevent a DDoS attack:- Deploy a CDN that absorbs traffic before it reaches your website to distribute the load of incoming traffic;
- Integrate DDoS protection plugins for WordPress with your site; and,
- Choose a hosting company that provides DDoS protection and guarantees their servers can manage a lot of traffic.
-
Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) involves attackers embedding malicious code into a website’s source code, usually targeting web page functionality. Once in, hackers can deceive visitors with cloaked links or fake forms to gather sensitive data.
This can lead to the loss or unauthorized use of sensitive data, like login passwords or personal information. It can also be used to launch additional attacks like phishing or the distribution of malware.
How to Solve This?
It is possible to reduce the risk of cross-site scripting vulnerabilities by improving data sanitization in a variety of ways. Encoding data as it leaves the system and filtering data as it enters can both be beneficial. Here are some best practices that can help you safeguard your WordPress site from XSS attacks:- Validate and clean up user input;
- Maintain current plugins and themes;
- Update the WordPress Core;
- Install a Web Application Firewall (WAF) to monitor traffic and stop unauthorized users from accessing your system.
Besides this, you can also use specific response headers to ensure that browsers know which data to read.
-
Cross-Site Request Forgery (CSRF)
Cross-site request forgery (CSRF) is a security vulnerability that enables attackers to trick users into doing things they don’t want to do. For instance, hackers can persuade users to do things like alter their email addresses, transfer money, change their passwords, etc.
Depending on the user’s actions, the attacker may be able to take over their account and cause havoc. CSRF can be devastating for entire applications if admin accounts are targeted. Hackers frequently deliver URLs through chat messages or emails while posing as legitimate users or administrators, perpetrating cross-site request forgery.
How to Solve This?
The focus of preventative measures is often on CSRF tokens, which are extremely challenging to guess and are specific to each user session. However, these help application servers determine whether requests are really created and are produced by the programme but shared with the client.You can also avoid CSRF attacks by carefully monitoring the plugins on your site. Installing a powerful WordPress security plugin can help you defend against cross-site request forgery and other attacks. You can also implement two-factor authentication, disable file editors, and block PHP execution in untrusted files to prevent CSRF attacks.
Lastly, since social engineering plays a significant role in CSRF attacks, education and security training are particularly crucial.
Final Thoughts
WordPress is one of the most reliable and powerful CMS platforms in the digital world. However, new and more advanced cyber threats are mushrooming by the minute, and without the right security knowledge, you may not be able to protect your site from hackers, viruses, and other malicious entities.
When it comes to WordPress security solutions, you can:
- Use security plugins and strong passwords,
- Activate two-factor authentication,
- Keep your software and themes up to date,
- Make regular backups and
- Pick a safe hosting provider.
Incorporating these best practices can go a long way toward helping you lower security risks.
That’s not all. Besides the eleven security vulnerabilities mentioned above, your WordPress website may be prone to several other issues, such as phishing, hotlinking, poor hosting, and more.
The best way to stay safe is to stay informed about the latest cybersecurity measures and updates. It is the ultimate way to protect your online presence, earn the trust of your customers, and grow your business.
Sapna Singhal Author
Sapna Singhal is a Freelance Content Writer who specializes in writing data-driven blog posts around B2B Marketing and SaaS. She writes content that only generates millions of traffic but also helps clients double down on their revenue. When she’s not writing, you can find her chit-chatting with her sisters or reading books!